Les investisseurs retrouvent un intérêt dans la nouvelle génération de startups qui se lancent dans la cybersécurité
Le marché de la cybersécurité connait un dynamisme sans précédent. C’est ce que révèle le rapport 2019 Cyber Defenders que vient de publier le cabinet CB Insights. Sur les deux dernières années, les records ont été battu en matière d’investissements dans les startups spécialisées en cybersécurité : 596 deals en 2017 pour un montant de 8 milliards de dollars, 601 deals pour 7 milliards en 2018. L’année dernière fut également une année record pour les rachats : plus de 80 entreprises IT n’ayant jamais procédé à une acquisition dans ce domaine l’on fait en 2018.
Dans cette activité sur la période 2014-2019, les Etats-Unis sont très largement en tête avec près des deux tiers des initiatives dans ce domaine devant Israël (6,7 %, le Royaume-Uni (6,5 %) et la Chine qui fait son entrée à la quatrième place.
Le rapport recense 8 licornes dans ce domaine très spécifique de la cybersécurité : 6 sont américaines (Tanium, Illumio, Cloudflare, Lookout, Crowstrike et netskope) et 2 sont chinoises (4Paradigm et Tongdun).
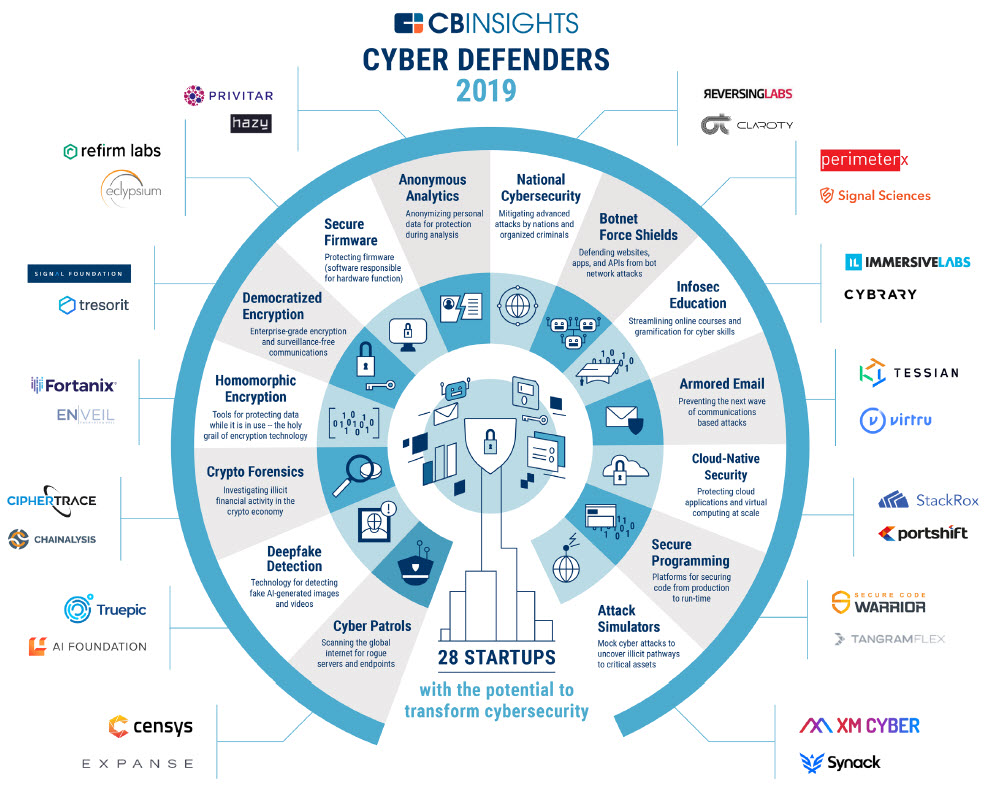
Le rapport classifie ce qu’elle appelle les cyberdefenders – 28 au total – en 14 catégrories qui devraient changer en profondeur le paysage de la cybersécurité et transformer aussi la manière avec laquelle les entreprises devraient se protéger dans le futur.
Détails sur les 14 catégories
| Cyber patrols | The enterprise attack surface is growing Devices, critical infrastructure, apps, and services connected to the internet are all potential network entry points that can be exploited by adversaries. |
| Deepfake detection | Deepfake (a portmanteau of « deeplearning » and « fake ») is type of fake synthetic image or video made with artificial intelligence. Deepfakes combine existing images and videosonto source images or videos using a machine learning technique called a generative adversarial network (GAN). |
| Crypto forensics | Bad actors are using cryptocurrency Cryptocurrencies such as Bitcoin enable money launderers and extortionists to obfuscate the origin and receipt of funds. Similarly, nations can use crypto to evade sanctions. |
| Homomorphic encryption | Data in use is the hardest to secure The enterprise data life cycle consists of three elements: data at rest, data in transit, and data in use. Traditional encryption secures data while it is at rest and in transit, but struggles to secure data in use. Actions like search and analytics have historically required decryption, creating points of exposure. |
| Democratized encryption | Encryption is essential for human rights Encryption enables freedoms of expression and privacy, and protects intellectual and digital property. However, access to high-grade encryption technology is rare and unevenly distributed. |
| Secure firmware | Firmware attacks could be devastating
Firmware is software that provides the low-level control for a device’s hardware functionality. Firmware threats are gaining speed in the wild,including remote and supply chain compromises that can destroy critical hardware that governs computer server functionality, and more. |
| Anonymous Analytics | Personal information needs protection Surveillance capitalism is the dominant paradigm shaping the way today’s internet giants make money. The world’s largest techcompanies and others increasingly profit from personal data. |
| National cybersecurity | Cyber threats are more advanced than ever Enterprises increasingly face threats from nations in cyber space. Among the top threats are espionage and extortion. Advanced hacking tools developed by the NSA and CIA have been leaked into the wild and made available to rogue nations and organized criminals. |
| Botnet force shields | Botnets are a rising threat Botnets are armies of networked, infected devicesthat simultaneously attack and overwhelm websites, online businesses, and other devices. Domain names registered solely to control botnets are skyrocketing. |
| Infosec education | Cybersecurity needs more qualified people There is a global shortage of qualified personnel available for employment in the cyber security industry. In fact, estimates say the world is short roughly 3 million cybersecurity professionals. |
| Armored email | Email is increasingly vulnerable Email continues to be the #1 threat facing IT security. Alongside the growth of email-based social engineering attacks known as phishing, other sophisticated email threats are rising. |
| Cloud-native security | Cybersecurity needs to be cloud-native Enterprises are migrating infrastructure and services to the cloud. In tandem, the complex virtual and legacy on-premise IT environmentsbeing created demand cybersecurity that is built for the cloud. |
| Secure programming | Some software can’t afford to fail Software operating inside critical infrastructure, autonomous vehicles, satellites, and more needs to work perfectly. Safeguarding mission critical software saves money and can prevent the loss of human life. |
| Attack simulators | The rise of active enterprise cyber defense We are witnessing a paradigm shift in enterprise cybersecurity. Organizations are shifting from passive defense to active defense, including embracing white-hats for simulating cyber attacks and more. |






 puis
puis